I upgraded to PHP 5.3.3 today, and I was shocked! I found a huge security hole default setting change that may leak the source code to public, which never happened in the earlier version.
Here is an example. Suppose my code looks like this:
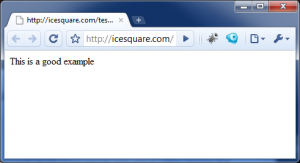
<?php echo "This is a good example"; ?>
Everything will turn out fine. Here is the result:
However, if the open tag is changed from <?php to <?:
<? //My comment echo "This is a bad example"; ?>
Then PHP 5.3.3 will not recognize the code within the < ? and ?> tag. Instead, it will parse it as a regular text file, i.e., your users will see the code. Here is the result:
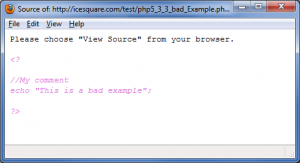
I know that it happens on PHP for Windows (XAMPP for Windows), but I didn’t know that they move this new feature to Unix world.
Update:
Thanks for the help from bt garner, it is pretty simple to fill this security hole.
First, open the php.ini. If you are not sure where is it, you can run the following command to locate it:
sudo find / -name "php.ini"
And activate the following parameters:
short_open_tag = On
That’s it!
–Derrick
Our sponsors:

You can override this behavior in the php.ini file. Just set:
short_open_tag = On
and the old tags will work just fine.
@bt garner: Thank you!!!