Recently I started using the Google One VPN service. I love it because of its simplicity. However, I quickly ran into problem because some services require my real IP addresses. Since the Google One VPN is designed for average Joe, it doesn’t have any advanced features. It is either all or nothing. Therefore I came up a way to solve this problem.
My goal is pretty simple. I want to enable/disable the VPN based on the application. For example, I want to disable VPN for my SSH client, my Remote Desktop, Portable Firefox, while I want to enable VPN for my another Portable Firefox and Google Chrome. My solution is pretty simple. I did this by creating a brunch of ports via SSH tunneling.
By default, Google One VPN routes most of traffics to the VPN based on the IP address you visit, with few exceptions, such as those on your local network (e.g., 192.168.1.X), or your own computer (e.g., 127.0.0.1). I realized that I can use this trick to achieve my goal. Of course, you will need another Linux/Mac/BSD computer or any server that support SSH to do it.
Goal #1: Using my real (home) IP address
In this case, my goal is very simple. I want to access certain websites using my real IP address. Here is the theory:
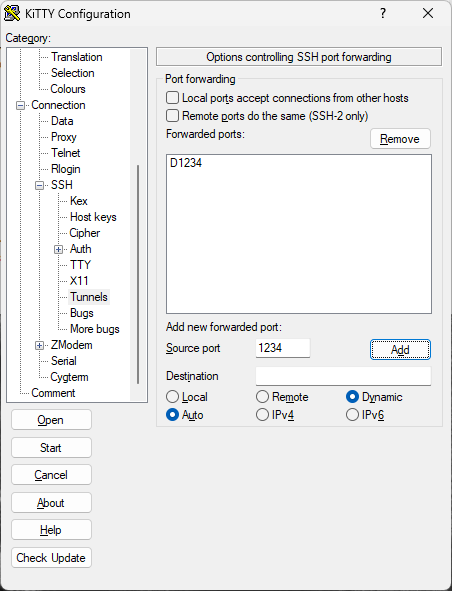
- I make a SSH connection to my local Linux box.
- I create a SSH tunnel, e.g., port 1234
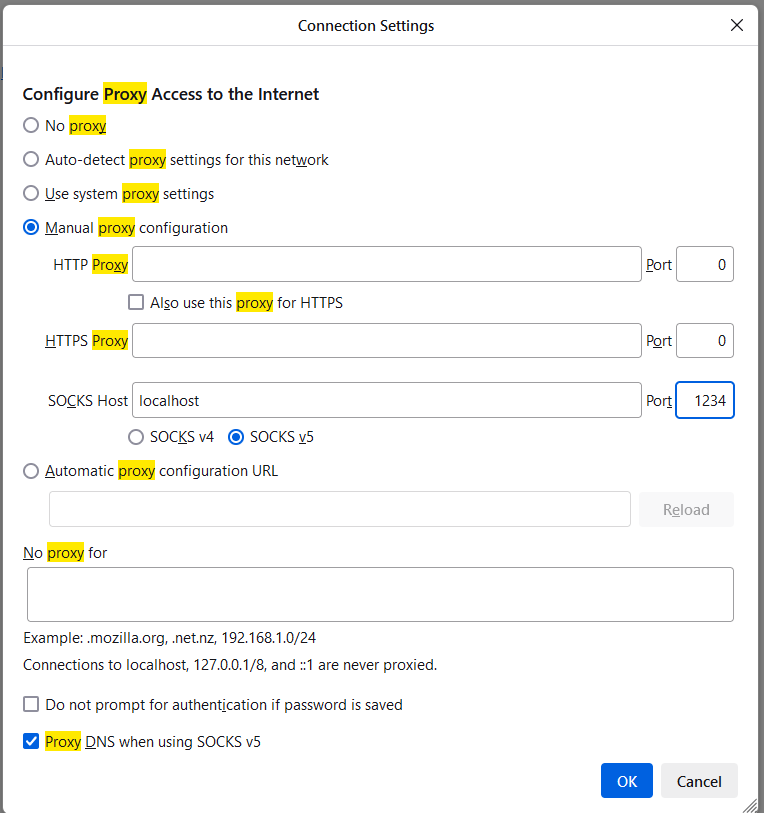
- For my application, I turn on the proxy option and route the traffic through that port, e.g., localhost:1234
Goal #2: Using my work IP address
In this case, I will need to SSH to my office front end server first. Then I create a number of SSH tunnels to connect to the devices/services in my work intranet. Notice that my office front end server has IP address restriction. It only allows certain IP addresses to make the connection. If I try to SSH to the server with my VPN IP address, it will be blocked. Even if I try to make the SSH connection before running the VPN software, my SSH connection will be disconnected after I turn on the VPN software. My solution is pretty simple. I route the traffic through my local Linux box.
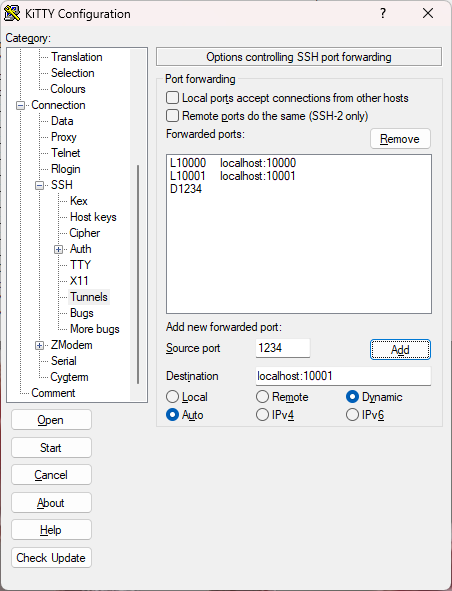
Suppose I need to connect to my office workstation. Previously, I connected to the front end server first (e.g., 123.123.123.1). I created two SSH tunnels, one for my Firefox to consume, so that I can access certain website using my office IP address, another one to access my office workstation (e.g., 10.0.0.101) via Remote Desktop.
The idea is pretty simple. When I SSH to my Linux box on my local server, I create two ports in my SSH client (e.g., Putty). Here is my setup. Notice that I create two ports: 10001 and 10002. These create two ports on my Windows computer. Putty will forward the traffic to my Linux box. To keep things simple, I use the same port number, e.g., port 10001 on my Windows points to the port 10001 on my Linux box.
Once I connect to my local Linux box, I run the following commands.
#This will create a tunnel for the web browser to consume, i.e., browsing the website using office IP address. #10001: The port created on the Linux box. #123.123.123.1: The IP of my office front end server. #This assumes that I can SSH to my office front end server using keys (no password) nohup ssh -C -D 10001 123.123.123.1 -N > /dev/null &
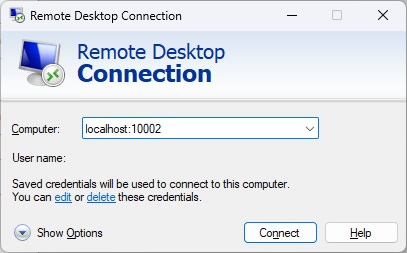
#This will create a tunnel for the Remote Desktop to consume, i.e., I can connect to my office workstation. #10002: The port created on the Linux box. #10.0.0.101: The local IP of my office workstation #3389: The port of my office workstation #123.123.123.1: The IP of my office front end server. #This assumes that I can SSH to my office front end server using keys (no password) nohup ssh -C -L 10002:10.0.0.101:3389 123.123.123.1 -N > /dev/null &
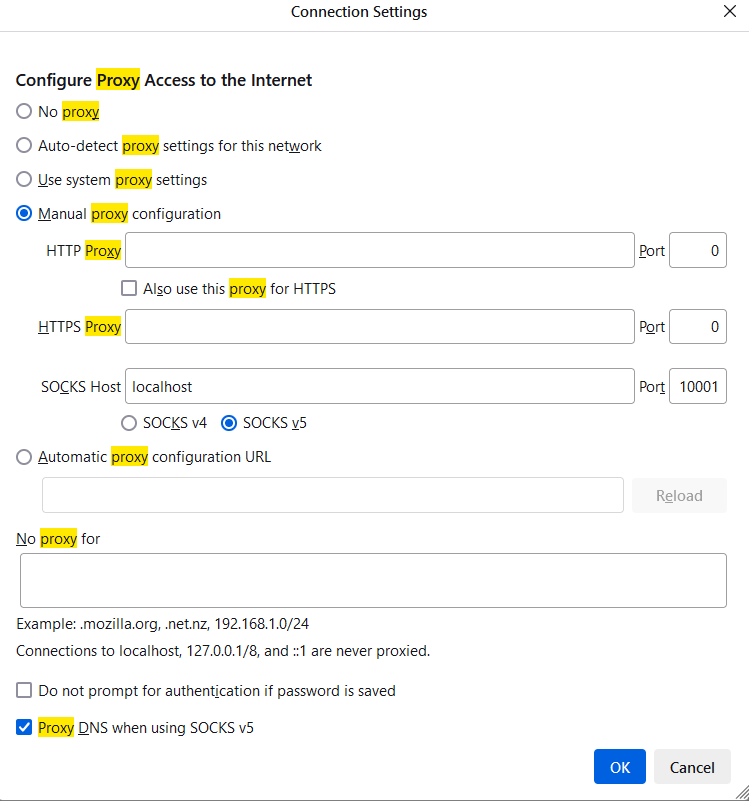
Here is my proxy settings of my Portable Firefox
When I connect to my office workstation, I can do the following:
That’s it, have fun with your VPN.
Our sponsors:
